The Last Password Can t Be Used Again When the User Changes a Password
A good password policy is the first step on securing your environment and company information. Without a countersign policy in place you tin can be certain that a lot of users will take a password that can be easily guessed/creature forced in less than 5 minutes. The tabular array beneath will testify the 5 most used passwords of 2019. Equally you can see, they are not rubber.
| 1 | 12345 |
| 2 | 123456 |
| 3 | 123456789 |
| iv | test1 |
| v | password |
Accept a look at the Microsoft Password Guidance for more data most passwords.
Azure Advertizing Only
Default password policy
When using Azure Agile Directory on its own (no on-premises AD with Azure Advertising Connect) you automatically make use of the Azure Advertizing password policy. Look at the requirements below or take a expect at the Microsoft documentation.
| Property | Requirements |
| Characters allowed | A – Z a – z 0 – 9 @ # $ % ^ & * – _ ! + = [ ] { } | \ : ' , . ? / ` ~ " ( ) ; blank space |
| Characters not allowed | Unicode characters. |
| Length constraints | A minimum of eight characters and a maximum of 256 characters. |
| Countersign restrictions | Requires three out of four of the following Lowercase characters. Uppercase characters. Numbers (0-9). Symbols (see the previous password restrictions). |
| Countersign expiry | Default value is 90 days. |
| Password decease notification | Default value is 14 days. |
| Password modify history | The last password can't exist used again when the user changes a password. |
| Countersign reset history | The final password tin can be used over again when the user resets a forgotten password. |
| Account lockout | After 10 unsuccessful sign-in attempts with the wrong password, the user is locked out for ane minute. Further incorrect sign-in attempts lock out the user for increasing durations of time. Smart lockout tracks the terminal three bad countersign hashes to avoid incrementing the lockout counter for the same password. If someone enters the same bad password multiple times, this behavior will not cause the account to lock out. |
On height of the requirements above all Azure AD tenants use Azure Advert Password Protection. This characteristic will eliminate all weak password by blocking known weak passwords.
Global banned countersign listing
Microsoft has a listing of global banned passwords that is kept upwardly-to-date by analyzing Azure Advertising security telemetry data. They expect for commonly used passwords that are weak and/or compromised. It'south important to note that Microsoft doesn't use third-political party/public password lists – all data is coming from Azure Advert itself.
Custom banned password list
It's possible to add together a custom banned password listing on top of the global list. This mode you lot can block passwords that are primarily focused on organizational-specific terms like brand names and product names.
Password evaluation
Microsoft uses the lists above to determine if a passwords is considered safe. To appraise the strength of a new password, Microsoft will become through a few steps and volition accepted or refuse based on the issue. You tin some bang-up documentation on this but i'll add together a cursory overview for completeness.
- Normalization is used to map a small prepare of passwords to a much larger set. They'll replace all upper-case letter messages with smallercase and common character substitutions are performed (an 'O' becomes an '0', an 'I' becomes a 'one', …)
- Fuzzy matching is applied on the normalized passwords, based on an edit distance of one comparing. If 'AzureScene' is on the countersign list and a users changes his password to 'BzureScene' the password is denied because it is within an edit distance of one of AzureScene.
- Substring matching is applied on the normalized passwords. Substring matching volition look for the first name, last name en tenant proper name in the password.
Subsequently applying all steps above a password score will be calculated. A score of at least 5 is required for the countersign to exist accepted.
- Each banned word is given 1 point.
- All remaining characters are given i point each.
How to meliorate?
Disable password expiration
Microsoft recommends disabling countersign expiration. Annotation that you should definitely configure multi-factor authentication before doing this!
- Navigate to the Microsoft 365 Admin Center and log on with a global administrator.
- Click on Settings followed by Security & Privacy.
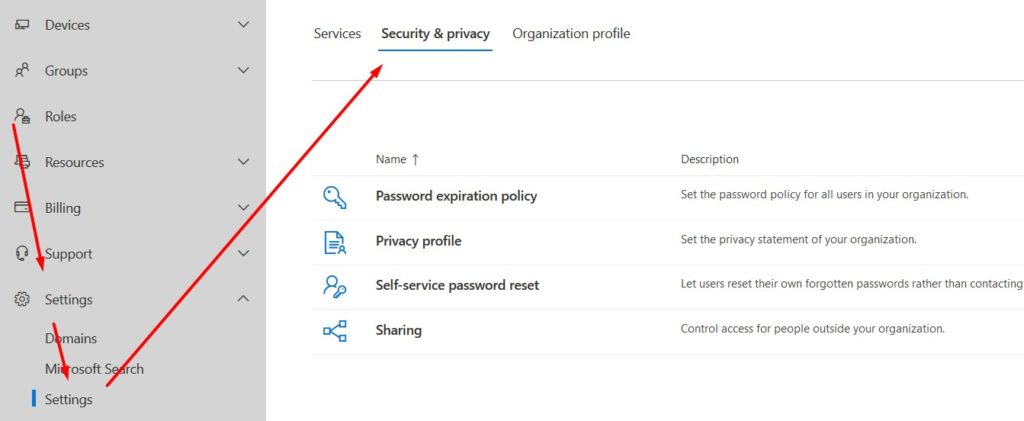
- Select Password expiration policy and deselect Set user passwords to expire afterwards a number of days.
Configure custom smart lockout settings
Smart lockout can block attackers who are trying to guess you lot users' passwords. Smart lockout can recognize sign-ins coming from valid users and therefore tin can lock out the assaulter while letting your users keep to access their accounts. Smart lockout is included in all Azure AD tenants but custom settings will require Azure AD P1 or P2.
- Navigate to the Azure portal and log on with an account that has appropriate permissions.
- Open the Azure Agile Directory blade and click Security. You lot'll notice this within the 'Manage' expanse.
- Select Hallmark methods.
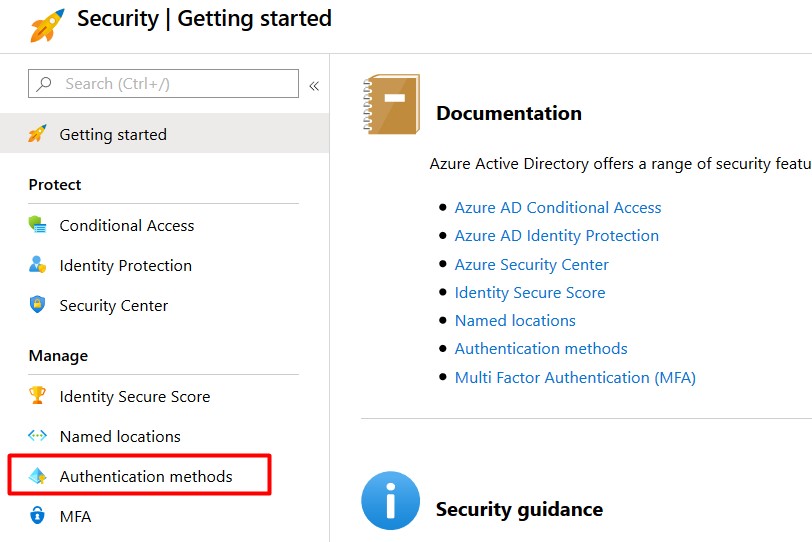
- Select Password protection.
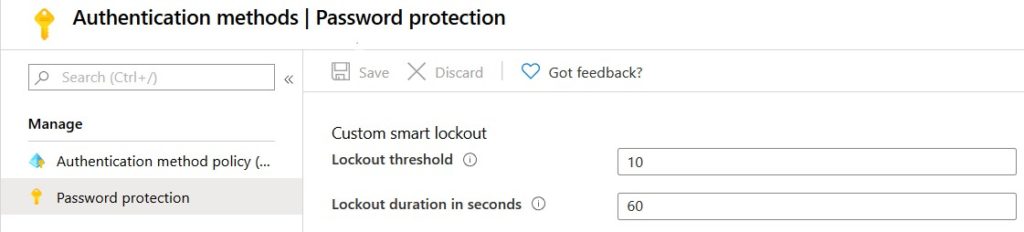
- Configure the lockoust threshold and lockout duration in seconds as desired. The default settings are pretty proficient to starting time (You don't need to practise anything to enable this).
Configure custom banned passwords
Customer banned passwords are configured in the same blade as custom smart lockout (expect in a higher place).
- Navigate to the Azure portal and log on with an account that has appropriate permissions.
- Open the Azure Active Directory bract and click Security. You'll discover this within the 'Manage' area.
- Select Hallmark methods.
- Select Countersign protection.
- Enable Enforce custom list.
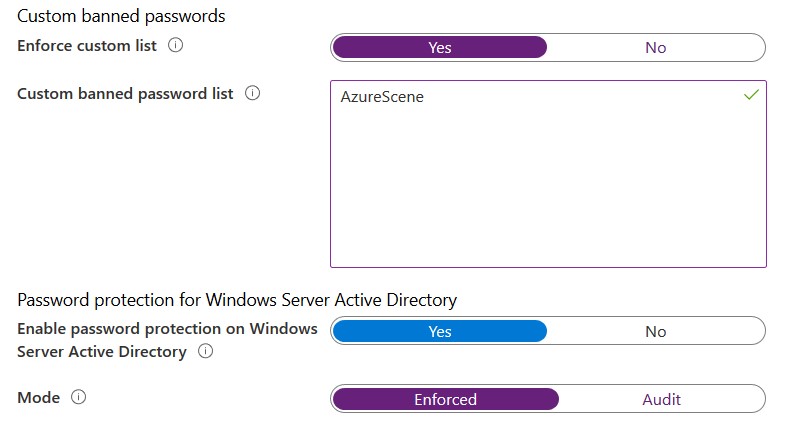
- Add words to your custome listing.
- Optionally: Enable password protection on Agile Directory. An amanuensis on your domain controller is required for this to work (look below).
- Set up the mode to Enforced.
Monitor users at risk
Configure Azure AD Identity Protection including email notifications to monitor leaked credentials, risky sign-ins and more. Look at my blog post on Azure AD Identity Protection for more information.
Enable self-service password reset
Self-service password reset gives your users the power to reset their password or unblock their account without a call to support.
Go passwordless
Microsoft recommends going passwordless. This feature is across the scope of this blog posts but will be added in the most futurity.
Active Directory & Azure Ad Connect
When using an on-premises Agile Directory the default Azure AD countersign policy isn't used. Without a local password policy, users tin can change their passwords to any they like and it will get synchronized to Azure AD. That'south why you lot must configure an on-premises password policy.
Configure on-bounds password policy
By default, every Agile Directory has a countersign policy in place. It'southward a calculator (non user!) setting in the Default Domain Policy. This policy will configure the active directory on all domain controllers to enforce the configured settings. Only i password policy is possible per domain and all users volition have the same password policy.
To edit the default password policy, you need to edit the Default Domain Policy. You can find all password settings under Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.

Enforce password history
This policy will set how many times a password tin be reused. There is no best practice but a minimum of v looks decent. When you set up passwords to not expire (every bit y'all should) 5 is perfect.
Maximum & minimum countersign age
Minimum password age will set the minimum amount of days a user needs to proceed his new countersign before information technology can be changed once more. The maximum password age will ready the days after which a countersign will elapse.
Disabling password expiration is the new standard. That'due south why Maximum password age should be set to '0'. The minimum password age should be set to one or more in order for for the password history setting to work.
Minimum password length
The minimum password length. A minimum of viii character will align this to the Azure Advertizement password policy. A countersign length under 7 is considered dangerous.
Passwords must meet complexity requirements
This setting should exist enabled. Passwords must run into the complexity described below.
- Not contain the user's business relationship name or parts of the user's total name that exceed two consecutive characters
- Contain charaters from 3 of the following categories.
- Uppercase characters (A – Z
- Lowercase characters (a – z)
- Base digits (0 – 9)
- Non-alphabetic charactesr (!$#%…)
Store passwords using reversible encryption
This should be disabled. When enabled, it's possible to decrypt all the encrypted passwords in AD.
Enable Azure AD Password Protection
It's possible to enable Azure AD Password protection for on-premises domain controllers. If configured, changing or resetting a password on-premises will use the same global and custom banned list as a password change in Azure Advertizement.
Azure AD Countersign Protection requires an agent to be installed on every domain controller. Password change/reset requests that are sent to a domain controller without the agent won't use password protection.
Installing the Azure AD Password Protection amanuensis is currently beyond the scope of this mail.
What about account lockout?
Enabling the account lockout policy seems similar a nice thought at offset but should non be taken lightly. An attacker that has access to a figurer in your domain can easily block everyone in minutes.
An aggressor can bank check the active countersign policy with a unproblematic command (net accounts /domain). No administrator permissions are required. If a lockout threshold is in place the attacker tin proceed on getting all users in the directory with another command that doesn't need ambassador permissions (wmic UserAccount Get Proper name).
Later getting al the users you can easily run a loop that will try to log on with every user of the listing and a random password. As shortly every bit yous hit the lockout threshold you're on to the adjacent one. The entire domain tin can be locked out in a matter of minutes.
In large environments I advise you to not configure an account lockout policy.
That'southward it, you're all gear up and a bit more secure!
Source: https://azurescene.com/2020/04/01/azure-ad-password-policy/
0 Response to "The Last Password Can t Be Used Again When the User Changes a Password"
Post a Comment